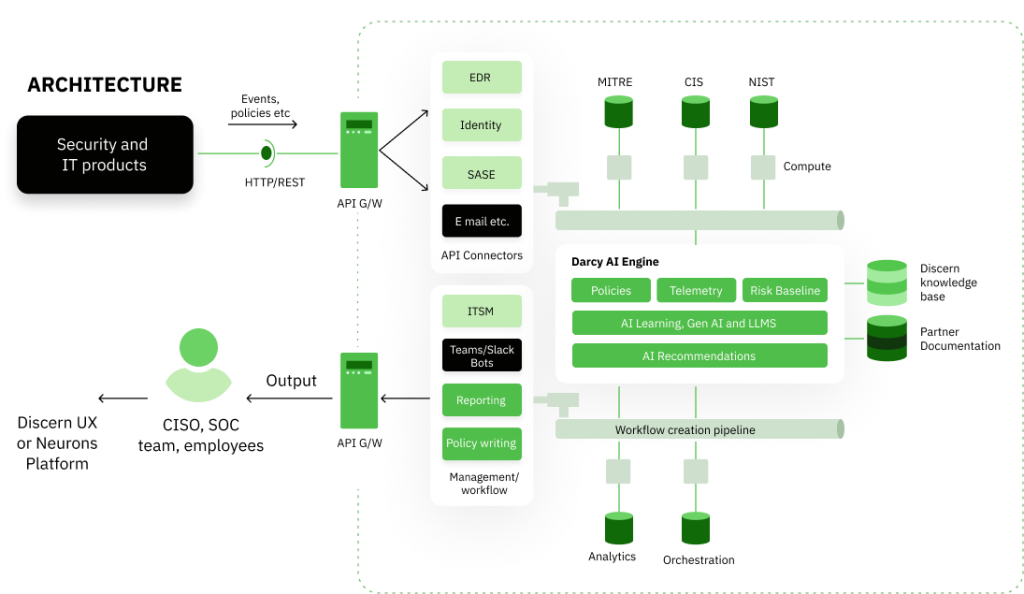
Build a cybersecurity mesh
that powers your organization's security
As cyber risks evolve, traditional security measures stagnate. Our innovative platform optimizes security configurations, enabling dynamic policy management across tools, bolstering defenses, and maximizing efficiency
Improve the ROI and efficacy of your security efforts
Business focused security narratives and reporting
Comprehensive dashboard, newsletters, cyber security tool report cards for CISO to share with various stakeholders
Cross platform intelligence
Curated actionable insights for CISOs
Automated policy management
Change Identity, Endpoint, SASE settings automatically based on uncovered insights
Triggering the right workflows
Call the right SOAR playbooks, raise the right tickets on ServiceNow and make easy policy approvals on Slack
Automated security posture improvements
Dynamically tailor security to specific users/devices and entities based on risk with access to fine grained security settings
Tangible ROI measurement
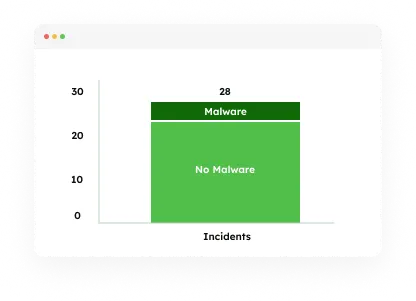
Progress reports and tangible ROI measurement with reduction in
malware, phishing and targeted users.
Stay ahead of the curve with real time compliance and threat assessment
Our compliance and threat assessment solutions are mapped to frameworks like MITRE ATT&CK® and D3FEND, NIST, CIS, and others to ensure that your security posture is dynamic and equipped to tackle the latest threats.
Our industry standard frameworks based compliance assessment
Provides a common language to understand and manage cyber threat
Helps decode attack cycle into TTPs commonly used by adversaries
Benchmarks against peers and relevant standards through actionable KPIs
Tackle the toughest questions on cyber risk with 360° visibility
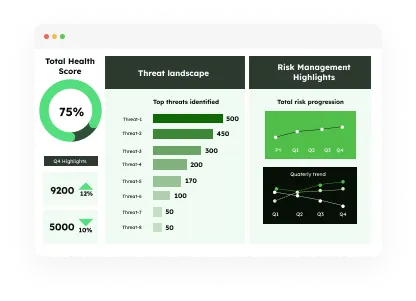
Visualize
Visualize endpoint health with our customized security configurations dashboard
Understand
Know the most critical threats, vulnerabilities, and compliance issues across IT configurations and assets
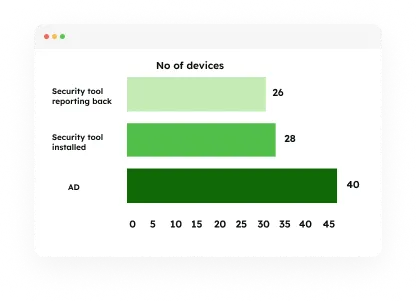
Prioritize
Focus on the 5% of users, devices and assets that account for over 90% of the risk
How we strengthen your
security posture
Step 1
We start by establishing a baseline for your security controls and configurations through seamless integration with your entire suite of security products
Step 2
Each of your security deployments undergoes a meticulous scoring process, evaluating both the effectiveness of controls and the associated risk factors.
Step 3
Leveraging our advanced generative AI, we address your critical security queries, providing you with actionable insights and personalized configuration recommendations tailored to your department and target users
Step 4
We dynamically map your security controls to established frameworks such as MITRE, CIS, and NIST, ensuring compliance. This not only showcases the progress of your security programs but also highlights their ROI
Step 5
Our ongoing commitment includes performing regular health checks to ensure that your security controls remain current in the face of evolving ransomware threats. We also verify that you are leveraging the latest features offered by your vendors for enhanced security